What is an SSRF?
SSRF stands for Server-Side Request Forgery. It's a vulnerability that allows a malicious user to cause the webserver to make an additional or edited HTTP request to the resource of the attacker's choosing.
Types of SSRF
There are two types of SSRF vulnerability; the first is a regular SSRF where data is returned to the attacker's screen. The second is a Blind SSRF vulnerability where an SSRF occurs, but no information is returned to the attacker's screen.
What's the impact?
A successful SSRF attack can result in any of the following:
- Access to unauthorised areas.
- Access to customer/organisational data.
- Ability to Scale to internal networks.
- Reveal authentication tokens/credentials.
Potential SSRF vulnerabilities can be spotted in web applications in many different ways. Here is an example of four common places to look:
When a full URL is used in a parameter in the address bar:

A hidden field in a form:
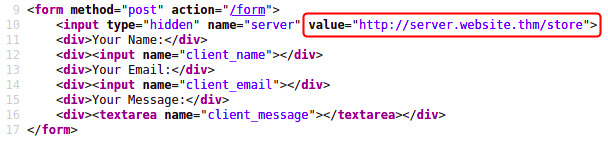
A partial URL such as just the hostname:

Or perhaps only the path of the URL:

Some of these examples are easier to exploit than others, and this is where a lot of trial and error will be required to find a working payload.
If working with a blind SSRF where no output is reflected back to you, you'll need to use an external HTTP logging tool to monitor requests such as requestbin.com, your own HTTP server or Burp Suite's Collaborator client.






0 comments:
Post a Comment