Buffer Overflow - Simply Explained with real world Example
A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold or when a program attempts to put data in a memory area past a buffer. In this case, a buffer is a sequential section of memory allocated to contain anything from a character string to an array of integers. Writing outside the bounds of a block of allocated memory can corrupt data, crash the program, or cause the execution of malicious code.
For better reference:
https://www.hackingtutorials.org/exploit-tutorials/buffer-overflow-explained-basics/
Lets say , we visit a signup page of a website and we entered email and password and click on signup . But before clicking sign up , I am capturing request in the Burp Suite . So when i captured the request , I changed email to some long string , like if email is "davinder@gmail.com" , i changed that to "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa@gmail.com" or even more in size
If i am able to proceed further without any restriction and or boundation, that this vulnerability exists.
Another example of code
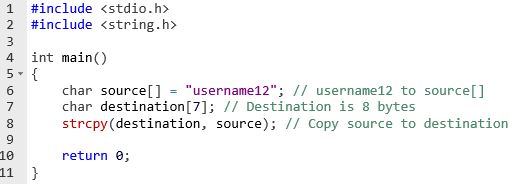
Steps to resolve:
Restrict size limit on input parameter.
Impact
Category:Availability: Buffer overflows generally lead to crashes. Other attacks leading to lack of availability are possible, including putting the program into an infinite loop.
Access control (instruction processing): Buffer overflows often can be used to execute arbitrary code, which is usually outside the scope of a program’s implicit security policy.
Other: When the consequence is arbitrary code execution, this can often be used to subvert any other security service.






0 comments:
Post a Comment